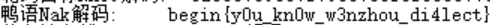第二届BeginCTF-WP

第二届BeginCTF-WP
hihopkcMISC
你知道中国文化嘛1.0
中国文化博大精深
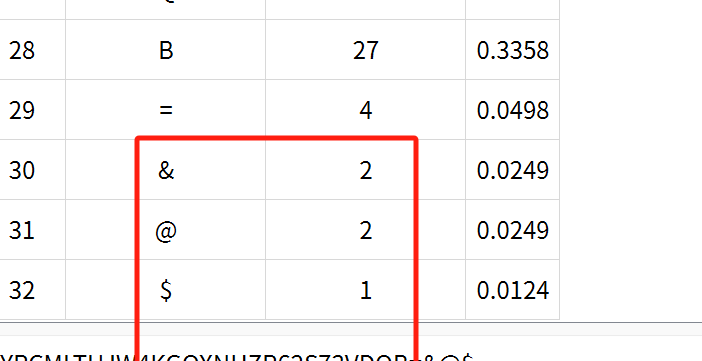
首先发现是”4km”一组,我们先拿一组解码发现是base32
全部复制进去,发现不对有其他字符
1 | $ -> S |
1 | 公正文明公正和谐公正平等文明友善法治和谐法治公正文明公正平等公正平等和谐爱国公正平等和谐和谐公正自由和谐爱国和谐富强和谐爱国公正公正公正和谐公正法治公正平等公正自由文明诚信和谐和谐文明公正平等公正公正和谐敬业和谐自由公正公正法治友善法治公正敬业法治友善平等公正民主和谐法治文明诚信和谐和谐民主和谐爱国文明诚信和谐和谐民主和谐文明公正友善爱国和谐爱国和谐民主公正和谐公正平等 |
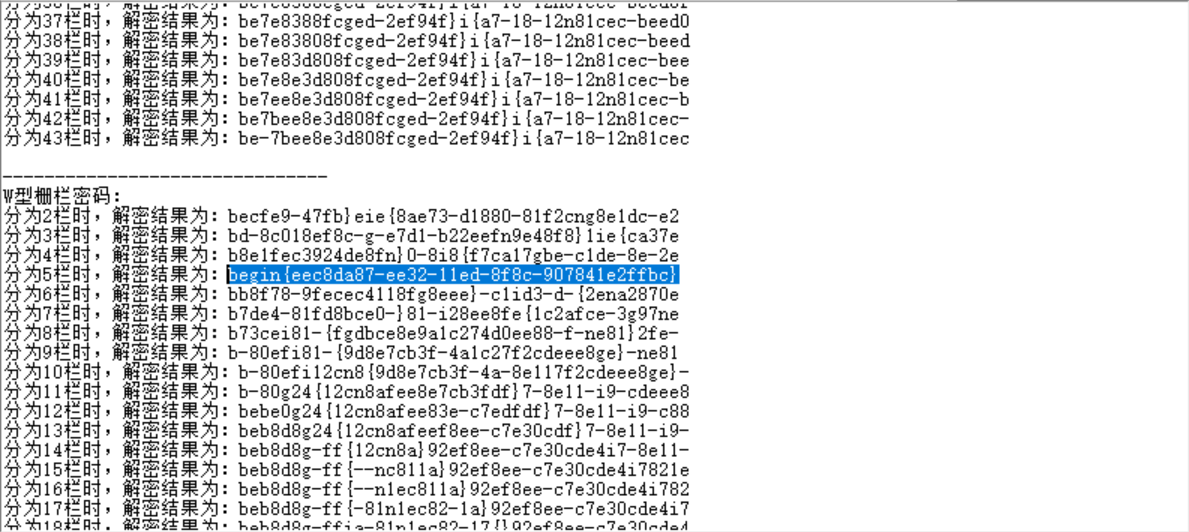
1 | bce-7bee8e3d808fcged-2ef94f}i{a7-18-12n81ce |
1 | begin{eec8da87-ee32-11ed-8f8c-907841e2ffbc} |
下一站上岸
某同学在考公的时候看到这样一道题,发现自己怎么也找不到图形的共同特征或规律你能帮帮他吗?
仔细观察下,有三种形态,第一种是完全在里面,还有一半,还有完全在外面
问了个考公同学,讨论后发现是交点有关,才分为三种
可以构造成
1 | 221022201122120120111011110222012101 |
解码为
1 | GO_ASHORE |
hgame{go_ashore}
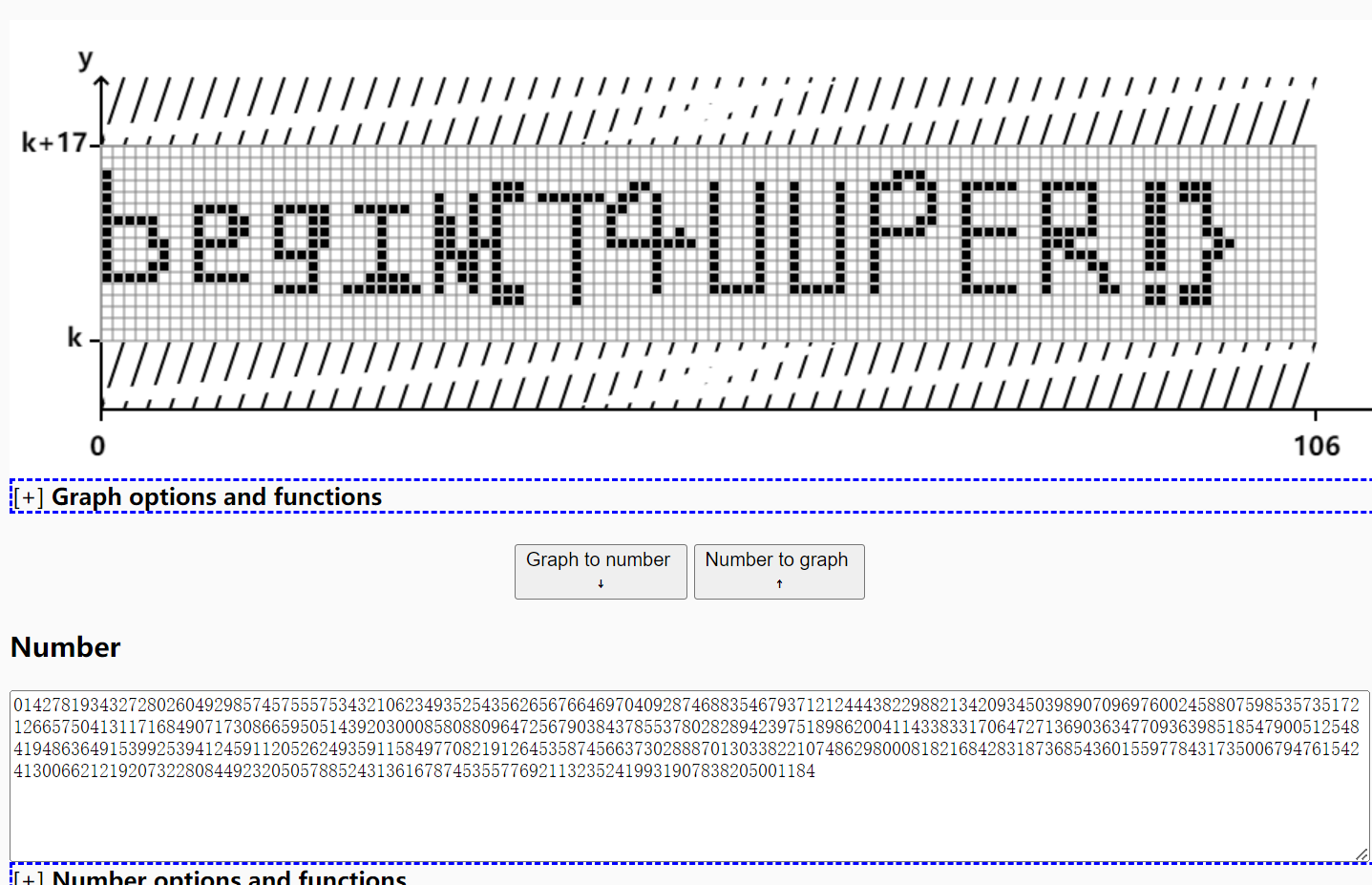
Tupper
1 | for i in range(0,676,4): |
1 | MTQyNzgxOTM0MzI3MjgwMjYwNDkyOTg1NzQ1NzU1NTc1MzQzMjEwNjIzNDkzNTI1NDM1NjI2NTY3NjY0Njk3MDQwOTI4NzQ2ODgzNTQ2NzkzNzEyMTI0NDQzODIyOTg4MjEzNDIwOTM0NTAzOTg5MDcwOTY5NzYwMDI0NTg4MDc1OTg1MzU3MzUxNzIxMjY2NTc1MDQxMzExNzE2ODQ5MDcxNzMwODY2NTk1MDUxNDM5MjAzMDAwODU4MDg4MDk2NDcyNTY3OTAzODQzNzg1NTM3ODAyODI4OTQyMzk3NTE4OTg2MjAwNDExNDMzODMzMTcwNjQ3MjcxMzY5MDM2MzQ3NzA5MzYzOTg1MTg1NDc5MDA1MTI1NDg0MTk0ODYzNjQ5MTUzOTkyNTM5NDEyNDU5MTEyMDUyNjI0OTM1OTExNTg0OTc3MDgyMTkxMjY0NTM1ODc0NTY2MzczMDI4ODg3MDEzMDMzODIyMTA3NDg2Mjk4MDAwODE4MjE2ODQyODMxODczNjg1NDM2MDE1NTk3Nzg0MzE3MzUwMDY3OTQ3NjE1NDI0MTMwMDY2MjEyMTkyMDczMjI4MDg0NDkyMzIwNTA1Nzg4NTI0MzEzNjE2Nzg3NDUzNTU3NzY5MjExMzIzNTI0MTk5MzE5MDc4MzgyMDUwMDExODQ= |
1 | 14278193432728026049298574575557534321062349352543562656766469704092874688354679371212444382298821342093450398907096976002458807598535735172126657504131171684907173086659505143920300085808809647256790384378553780282894239751898620041143383317064727136903634770936398518547900512548419486364915399253941245911205262493591158497708219126453587456637302888701303382210748629800081821684283187368543601559778431735006794761542413006621219207322808449232050578852431361678745355776921132352419931907838205001184 |
一想到题目tupper
https://blog.csdn.net/weixin_44143678/article/details/119869423
begin{T4UUPER!}
devil’s word
1 | leu lia leu ng leu cai leu jau leu e cai b cai jau sa leng cai ng ng f leu b leu e sa leng cai cai ng f cai cai sa sa leu e cai a leu bo leu f cai ng ng f leu sii leu jau sa sii leu c leu ng leu sa cai sii cai d |
1 | lia = 2 |
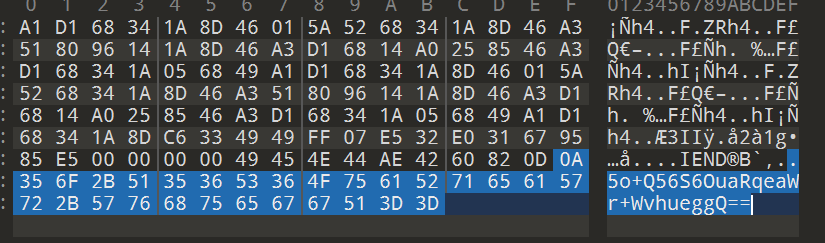
1 | 626567696e7b7930755f6b6e30775f77336e7a686f755f6469346c6563747d |
鸭语Nak解码: begin{y0u_kn0w_w3nzhou_di4lect}
where is crazyman v1.0
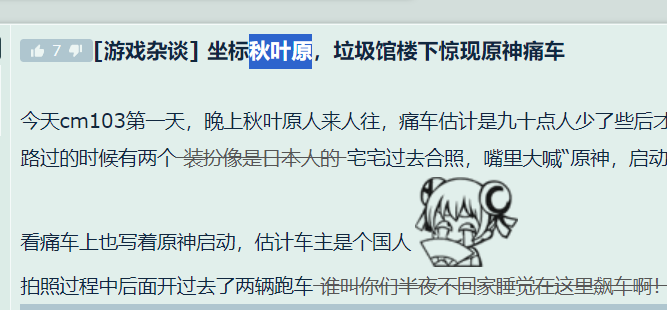
begin{秋叶原}
where is crazyman v2.0
真的想骂自己,旁边一直有,我一直看下面的东京……
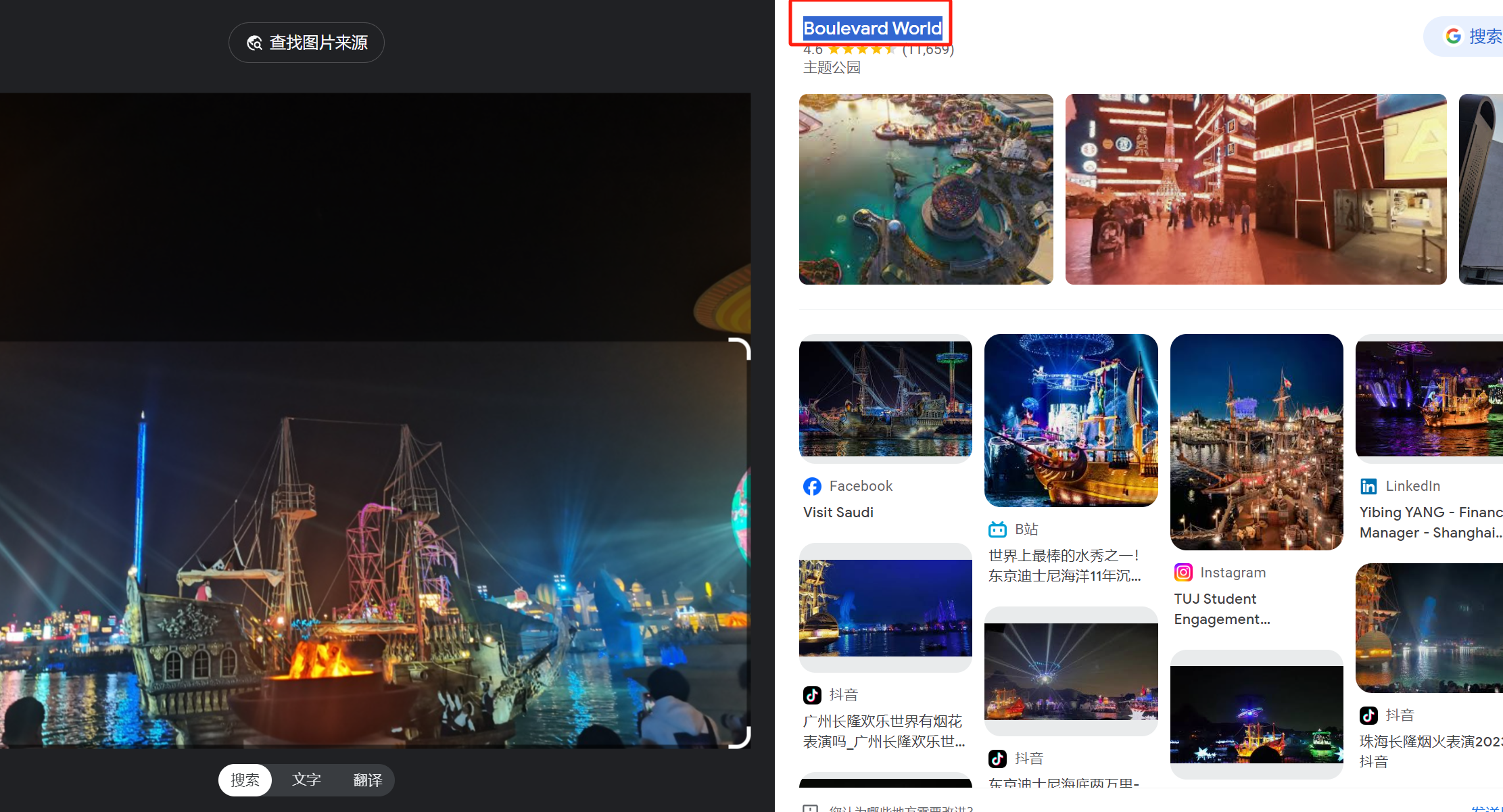
begin{Boulevard World}
where is crazyman v3.0
1.flag和地址没有直接关系 请不要提交地址 也不在所给图片里 不存在任何形式隐写 请使用OSINT工具和相关的方法找到flag
2.先找到地址再拿到flag秘密指得是隐藏的flag
3.如果需要确定地址 请找crazyman
4.星巴克和酒店很近 步行不到7min
星巴克,瓶子还有Boudl Apart Hotel
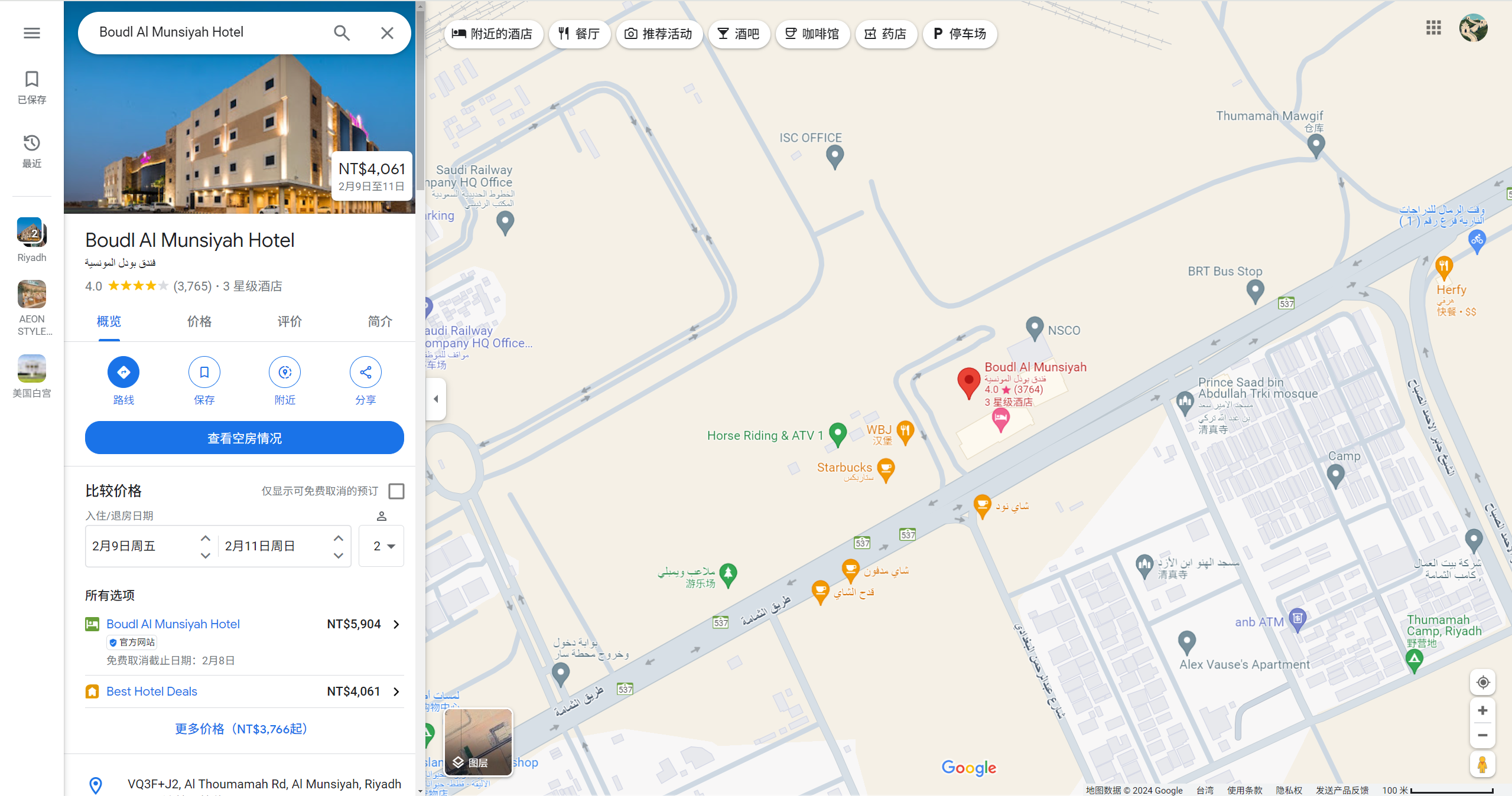
首先谷歌地图搜Boudl Apart Hotel搜到下面这个
然后搜索附近的starbucks
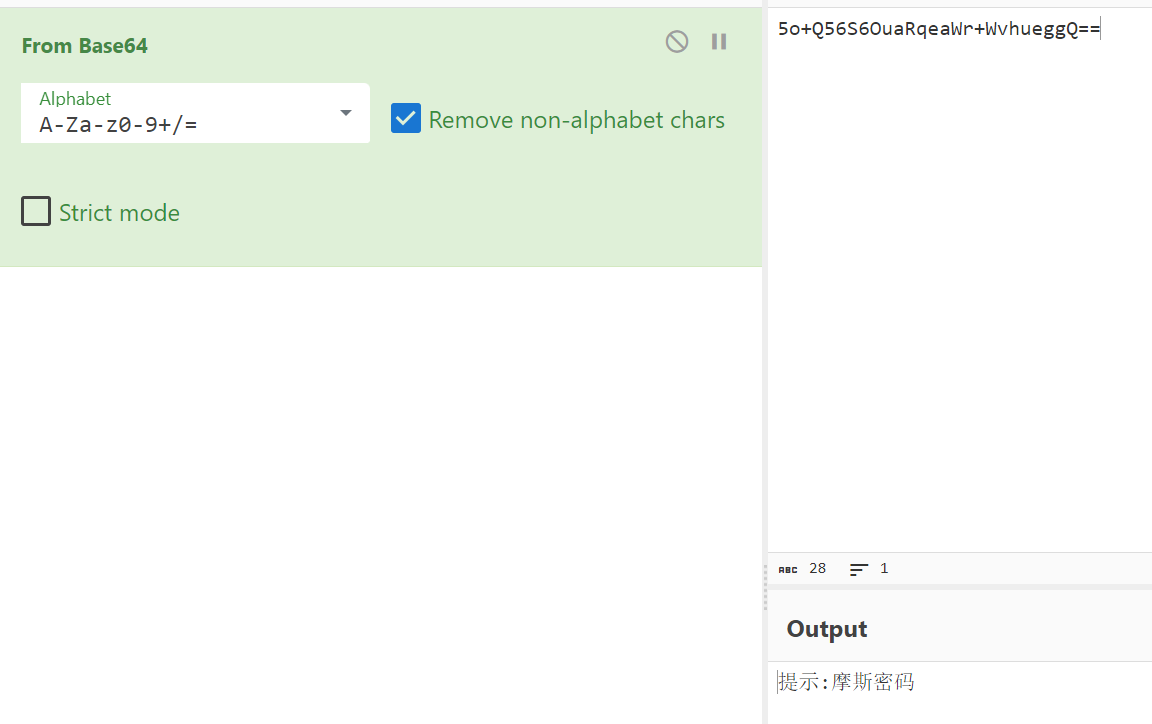
1 | YmVnaW57R29vZ2xlX21hcF9pc191c2VmdWxfYW5kX25vdF9mb3JnZXRfY29tbWVudH0= |
begin{Google_map_is_useful_and_not_forget_comment}
Forensics
dump dump dump
1 | dumpv1>strings dumpv1.DMP | grep flag.txt |
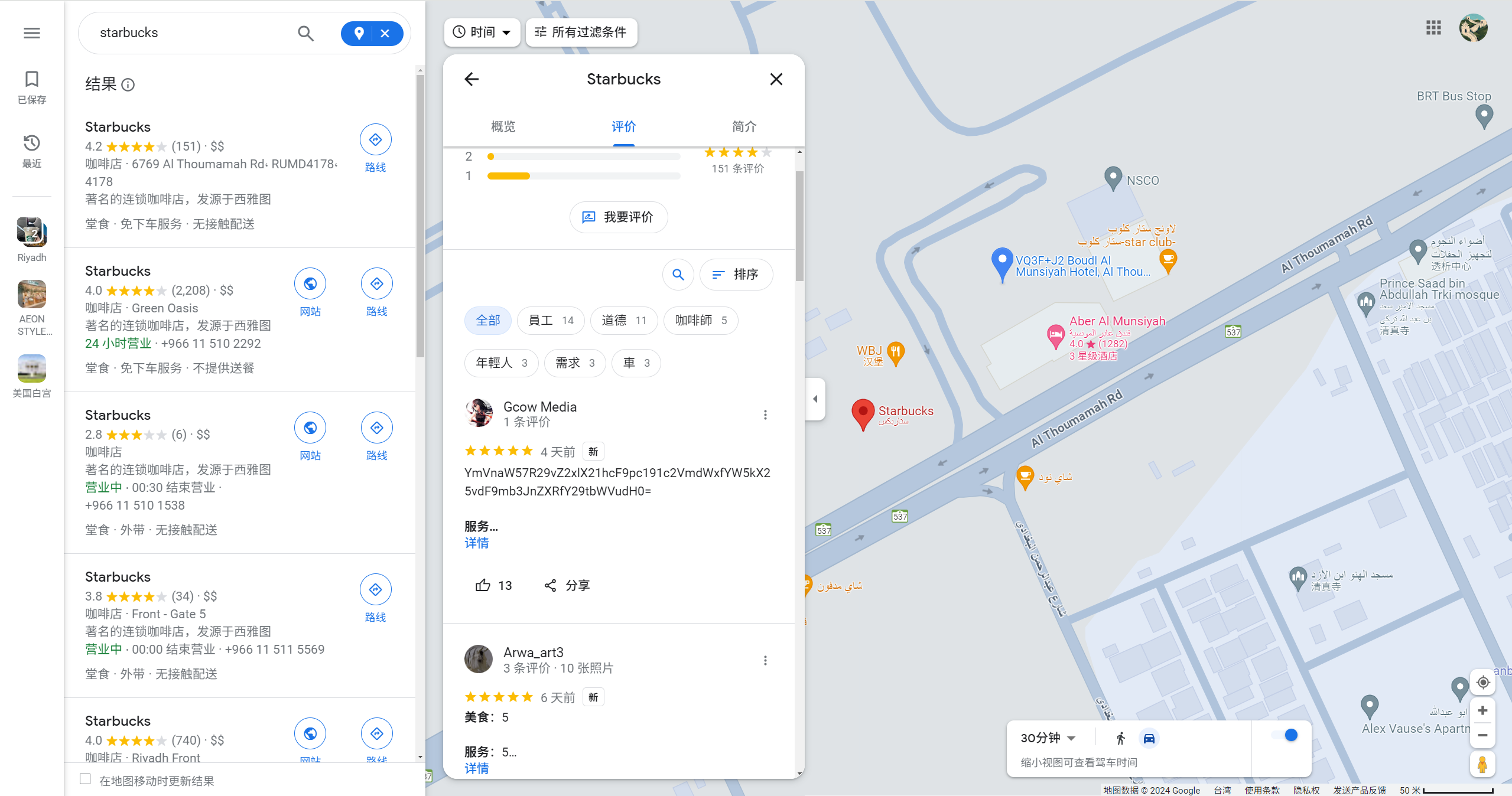
学取证咯 - cmd
1.你在我的电脑上干了什么?快使用volatility看一看cmd吧(将
flag格式改为begin{})
1 | vol.exe -f 学取证咯.raw --profile=Win7SP1x64 cmdscan |
begin{Cmd_1in3_109_i5_imp0rt@nt}
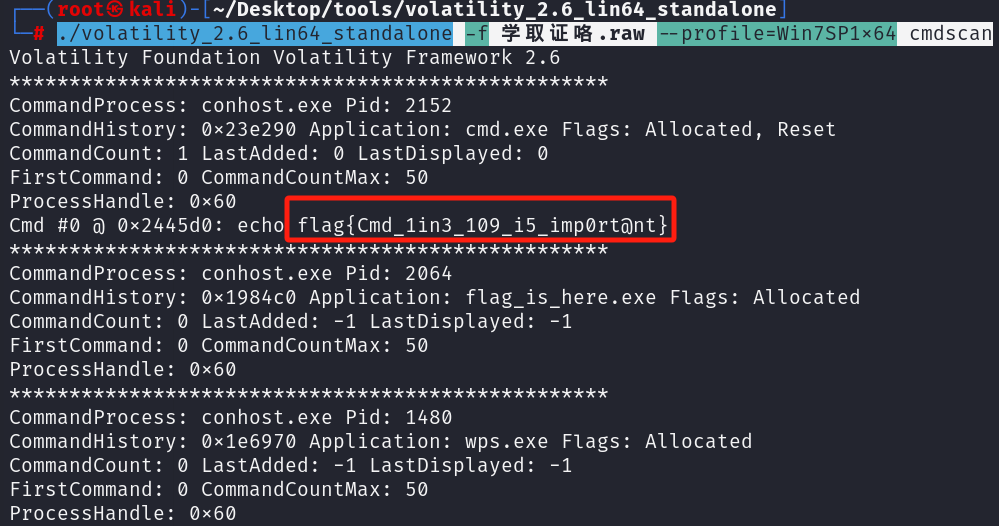
学取证咯 - 还记得ie吗?
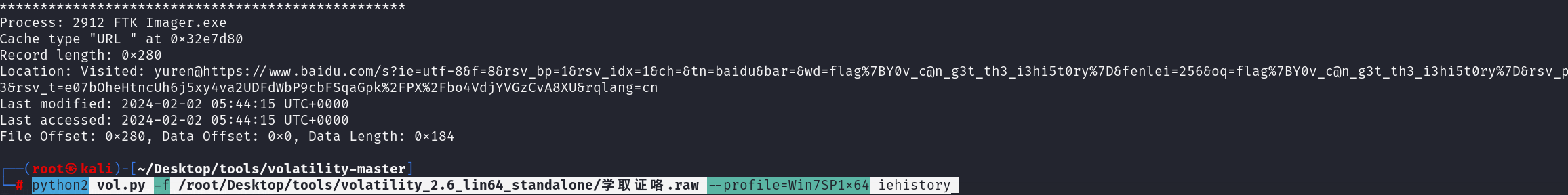
2.等一下,你的浏览器记录还没删。。。(将flag格式改为begin{})
1 | python2 vol.py -f 学取证咯.raw --profile=Win7SP1x64 iehistory |
1 | https://www.baidu.com/s?ie=utf-8&f=8&rsv_bp=1&rsv_idx=1&ch=&tn=baidu&bar=&wd=flag%7BY0v_c@n_g3t_th3_i3hi5t0ry%7D&fenlei=256&oq=flag%7BY0v_c@n_g3t_th3_i3hi5t0ry%7D&rsv_pq=ba856c22001a9d03&rsv_t=e07bOheHtncUh6j5xy4va2UDFdWbP9cbFSqaGpk%2FPX%2Fbo4VdjYVGzCvA8XU&rqlang=cn |
begin{Y0v_c@n_g3t_th3_i3hi5t0ry}
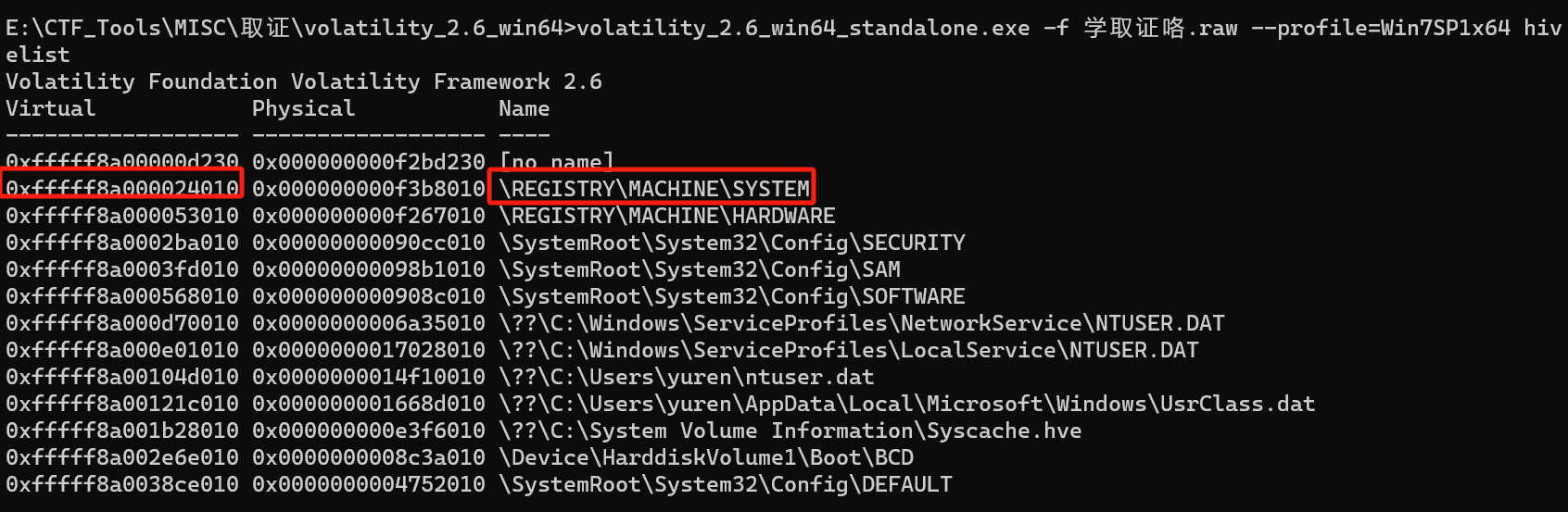
学取证咯 - 计算机的姓名?
3.想要知道WORKGROUP的名字捏(提交时外面包上
begin{})
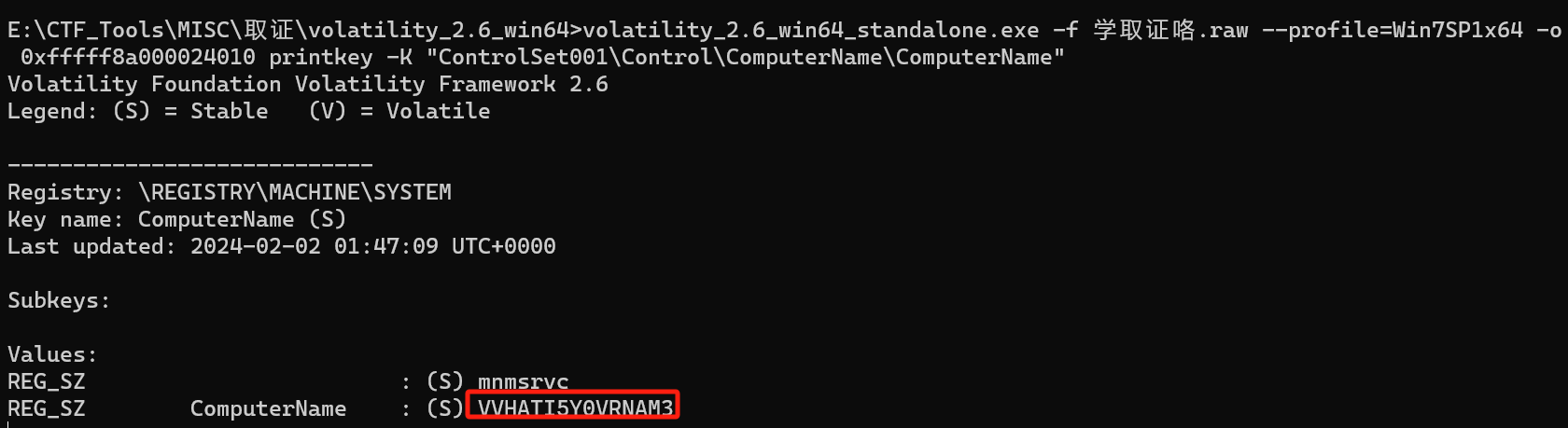
1 | volatility_2.6_win64_standalone.exe -f 学取证咯.raw --profile=Win7SP1x64 hivelist |
1 | volatility_2.6_win64_standalone.exe -f 学取证咯.raw --profile=Win7SP1x64 -o 0xfffff8a000024010 printkey -K "ControlSet001\Control\ComputerName\ComputerName" |
begin{VVHATI5Y0VRNAM3}
学取证咯 - 想登录我的计算机吗?
4.想登录我的计算机吗?我可不会告诉你登录口令(将
flag格式改为begin{})
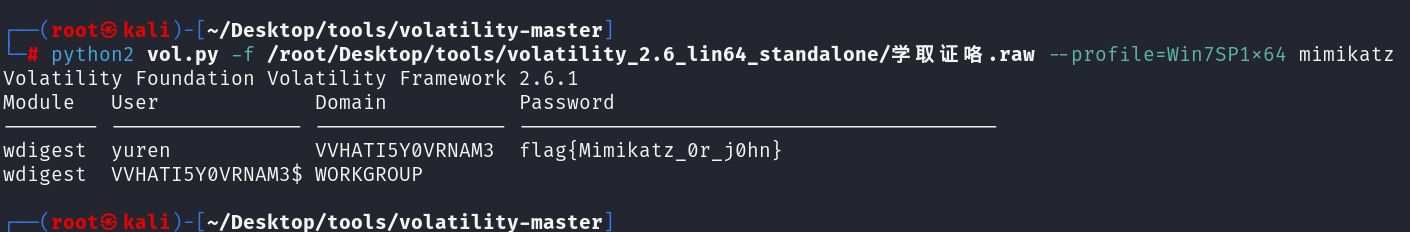
1 | python2 vol.py -f 学取证咯.raw --profile=Win7SP1x64 mimikatz |
begin{Mimikatz_0r_j0hn}
学取证咯 - 机密文件
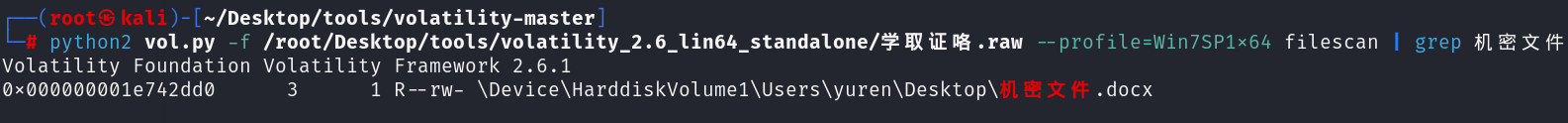
5.你能获取yuren在电脑中的机密文件吗(将flag格式改为begin{})
1 | python2 vol.py -f 学取证咯.raw --profile=Win7SP1x64 filescan | grep 机密文件 |
1 | python2 vol.py -f 学取证咯.raw --profile=Win7SP1x64 dumpfile -Q 0x000000001e742dd0 -D ./ |
得到
1 | flag{Y0v_c@n_d0vvn_th3_fi13}!!!!!!!! |
begin{Y0v_c@n_d0vvn_th3_fi13}
学取证咯 - 真的是取证吗?
6.请获取问题程序中的关键信息(将flag格式改为
begin{})
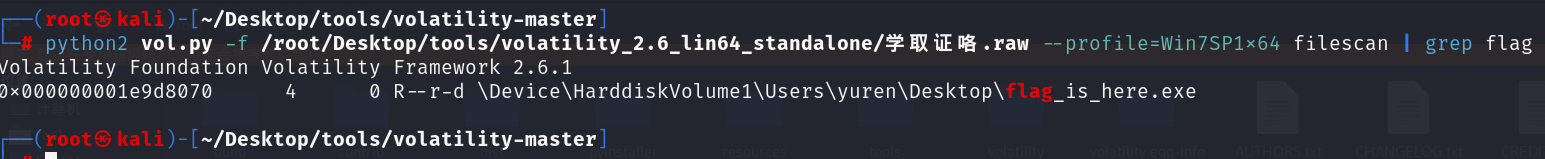
1 | python2 vol.py -f /root/Desktop/tools/volatility_2.6_lin64_standalone/学取证咯.raw --profile=Win7SP1x64 filescan | grep flag |
1 | python2 vol.py -f 学取证咯.raw --profile=Win7SP1x64 dumpfile -Q 0x000000001e9d8070 -D ./ |
Reberse
real checkin xor
1 | import string |
1 | secret = [7, 31, 56, 25, 23, 15, 91, 21, 49, 15, 33, 88, 26, 48, 60, 58, 4, 86, 36, 64, 23, 54, 63, 0, 54, 22, 6, 55, 59, 38, 108, 39, 45, 23, 102, 27, 11, 56, 32, 0, 82, 24] |
begin{3z_PY7hoN_r3V3rSE_For_TH3_Be9inNEr!}